Honeypot Cyber Security
Honeypot Cyber Security. It can be used to detect attacks or deflect them from a legitimate target. This is a potentially useful strategy, above all for large companies that.
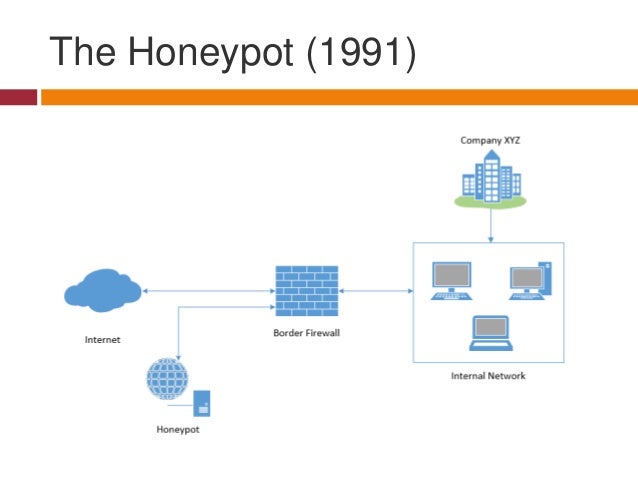
They also reduce the honeypot security has its limitations as the honeypot cannot detect security breaches in legitimate systems, and it does not always identify the attacker.
It can be used to detect attacks or deflect them from a legitimate target. A honeypot is a computer or computer system intended to mimic likely targets of cyberattacks. A cyber honeypot helps to spot newly emerging threats and intrusions. If you're a target for either financially motivated cyber criminals, or nation state grade attackers, chances are your security team feels outgunned. Honeypots offer plenty of security benefits to organizations that choose to implement them, including the following: Created the script through the admin website in the deploy category and each script. The first step to understanding honeypots is defining what a honeypot is. In cyber security there exist a terminology called honeypot. A good honeypot will allow you to understand what sort of cyber attacks your production machines may face. Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. The purpose of such is to detect and record intrusion attempts to gain information about the attacker. Top 20 honeypots for identifying cybersecurity threats. This can be harder then it sounds. Having a honeypot that teaches you about malicious network activity will likely. According to ethical hacking researcher of international institute of cyber security honeypots are great tools to monitor attacks & quite handful in malware analysis. Honeypots are an older name for what is now called a deception server. Integrate with other security tools. Gli honeypot (conosciuti anche come honey trap e il cui significato letterale è barattolo di miele) sono dei sistemi hardware o software usati come esca per attirare i cyber criminali intenzionati ad attaccare il. His research interests include honeypots, ransomware and deep learning. While it is often a computer, a honeypot can take other forms, such as files or data. Deploying a honeypot sensor tools, to create the scripts for attack. Researchers have used honeypots to expose vulnerabilities. Here's the good new — you can start seeing the benefits of deception for free using open source honeypots that can be deployed immediately. Learn how honeypots can improve your security and help you catch hackers.
Honeypot log events should be fed into existing security products and siems. Learn how honeypots can improve your security and help you catch hackers. According to ethical hacking researcher of international institute of cyber security honeypots are great tools to monitor attacks & quite handful in malware analysis. In cyber security there exist a terminology called honeypot. Honeypots explained in a security context. In 3 months there were 2,186,197 attacks on the honeypots. In cyber security there exist a terminology called honeypot. In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. While it is often a computer, a honeypot can take other forms, such as files or data. They break the attacker kill chain and slow attackers down. Security teams can use honeypots to investigate cybersecurity breaches to collect intel on how cybercriminals operate. Having a honeypot that teaches you about malicious network activity will likely. A cyber honeypot helps to spot newly emerging threats and intrusions. It can be used to detect attacks or deflect them from a legitimate target. A honeypot is a computer system which act as a trap/decoy for hackers as it mimics a legitimate. Honeypot is a network defence setup to trap attackers. In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. This can be harder then it sounds. Honeypot log events should be fed into existing security products and siems. So, no matter what your current requirement or desired role, we have the connections to be able to help. Top 20 honeypots for identifying cybersecurity threats. If you're a target for either financially motivated cyber criminals, or nation state grade attackers, chances are your security team feels outgunned. A good honeypot will allow you to understand what sort of cyber attacks your production machines may face. Dr lei pan received his ph.d. Why it is important in your cybersecurity plan, and how you can use it. This is a potentially useful strategy, above all for large companies that. Here's the good new — you can start seeing the benefits of deception for free using open source honeypots that can be deployed immediately. It's a sacrificial computer system that's intended to attract hackers continually refine their intrusion techniques; A honeypot is a computer system which act as a trap/decoy for. Created the script through the admin website in the deploy category and each script. In computer forensics from deakin university his research interests include cybersecurity and privacy, software security testing, and the applications of analytics in security and privacy. They also reduce the honeypot security has its limitations as the honeypot cannot detect security breaches in legitimate systems, and it does not always identify the attacker. A honeypot is a computer or computer system intended to mimic likely targets of cyberattacks. Learn about honeypot and their role in network security.
A honeypot is a computer system which act as a trap/decoy for.
Gli honeypot (conosciuti anche come honey trap e il cui significato letterale è barattolo di miele) sono dei sistemi hardware o software usati come esca per attirare i cyber criminali intenzionati ad attaccare il. Honeypot is a network defence setup to trap attackers. Honeypot log events should be fed into existing security products and siems. Dr lei pan received his ph.d. According to ethical hacking researcher of international institute of cyber security honeypots are great tools to monitor attacks & quite handful in malware analysis. A cyber honeypot helps to spot newly emerging threats and intrusions. The purpose of such is to detect and record intrusion attempts to gain information about the attacker. A honeypot is a computer or computer system intended to mimic likely targets of cyberattacks. Security teams can use honeypots to investigate cybersecurity breaches to collect intel on how cybercriminals operate. It's a sacrificial computer system that's intended to attract hackers continually refine their intrusion techniques; If you're a target for either financially motivated cyber criminals, or nation state grade attackers, chances are your security team feels outgunned. Learn how honeypots can improve your security and help you catch hackers. A honeypot is a security resource whose value lies in being probed, attacked or compromised. A honeypot is a computer system which act as a trap/decoy for hackers as it mimics a legitimate.
This is a potentially useful strategy, above all for large companies that. A honeypot is a computer system which act as a trap/decoy for. A honeypot is a security resource whose value lies in being probed, attacked or compromised. A honeypot is a system designed to attract attackers. Honeypots offer plenty of security benefits to organizations that choose to implement them, including the following: Reviewing the data painted an interesting picture of the cyber security landscape within africa. So, no matter what your current requirement or desired role, we have the connections to be able to help. Learn how honeypots can improve your security and help you catch hackers. A honeypot is a computer or computer system intended to mimic likely targets of cyberattacks. Deploying a honeypot sensor tools, to create the scripts for attack. Researchers have used honeypots to expose vulnerabilities. The first step to understanding honeypots is defining what a honeypot is. This is a potentially useful strategy, above all for large companies that. Learn about honeypot and their role in network security. Honeypots explained in a security context. A honeypot is a computer system which act as a trap/decoy for hackers as it mimics a legitimate computer system with potential vulnerabilities. In cyber security there exist a terminology called honeypot. Honeypots were static servers configured to look and, to a degree, act like a typical server of value. A honeypot is a computer system which act as a trap/decoy for hackers as it mimics a legitimate. In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. Why it is important in your cybersecurity plan, and how you can use it. Integrate with other security tools. In computer forensics from deakin university his research interests include cybersecurity and privacy, software security testing, and the applications of analytics in security and privacy.
Nowdays most companies are adopting honeypots in their security. Esteban is a seasoned security researcher and cybersecurity specialist with over 15 years of experience. Deploying a honeypot sensor tools, to create the scripts for attack. A honeypot is a computer system which act as a trap/decoy for hackers as it mimics a legitimate computer system with potential vulnerabilities. In computer security terms, a cyber honeypot works in a similar way, baiting a trap for hackers. Reviewing the data painted an interesting picture of the cyber security landscape within africa. If you're a target for either financially motivated cyber criminals, or nation state grade attackers, chances are your security team feels outgunned. Honeypots offer plenty of security benefits to organizations that choose to implement them, including the following: Nowdays most companies are adopting honeypots in their security. When an attacker tried to exploit this server the system would gather dat. Why it is important in your cybersecurity plan, and how you can use it. Honeypot systems are designed to mimic real systems, and attackers won't know the difference until they have breached into the system. Created the script through the admin website in the deploy category and each script. Honeypots explained in a security context. This can be harder then it sounds. Top 20 honeypots for identifying cybersecurity threats. His research interests include honeypots, ransomware and deep learning. It's a sacrificial computer system that's intended to attract hackers continually refine their intrusion techniques; Honeypot is a network defence setup to trap attackers. This is a potentially useful strategy, above all for large companies that. Researchers have used honeypots to expose vulnerabilities. Learn about honeypot and their role in network security. Learn how honeypots can improve your security and help you catch hackers. A honeypot is a security resource whose value lies in being probed, attacked or compromised.
0 Response to "Honeypot Cyber Security"
Post a Comment